Configuring SAML/ADFS Authentication for a Tenant
After the master administrator has configured Platform to enable SAML/ADFS authentication, the tenant administrator must follow these steps to configure SAML or ADFS authentication details for the tenant:
- Configure your IdP to add values for your Platform tenant.
These values include the following; different IdPs might have different labels for
these. The labels shown below are for Salesforce:
- Entity ID — The value of the
entityIDattribute of theEntityDescriptorelement in the SP metadata file - ACS (Assertion Consumer Service) URL — The value of the SAML ACS(Assertion
Consumer Service) URL property on the SAML/ADFS configuration page in
Platform
- To allow SP and IdP initiated login, use the entire ACS URL, lets
say
http://hostname/router/login/loginSaml/8011/c3649e5b-8112-43ad-bf2f-dfad6c0a81a0 - To allow SP only initiated login, use the partial ACS URL till the
custId, lets sayhttp://hostname/router/login/loginSaml/8011
- To allow SP and IdP initiated login, use the entire ACS URL, lets
say
- Encrypt SAML response — Upload the public key certificate file. The master administrator should provide you with this file.
- Entity ID — The value of the
- After configuring the IdP, obtain the IdP's SAML/ADFS metadata XML. You will need to save this as a file and use it in the next step. This is usually provided by the IdP as either a file or as a URL containing the metadata XML. If it is provided as a URL, save the XML in a file anywhere on your machine. This file is referred to as the IdP metadata file in the next step. See Configuring the Platform instance to enable SAML/ADFS authentication for more information.
-
Select SAML/ADFS as the authentication method as described in Creating an Authentication Profile.
You can also specify the values for the following fields in Authentication Settings section of Administrative Preferences to configure SAML/ADFS authentication.
Field Description SPKey Store File The name of the keystore. In the prerequisite steps example, InfiniteBlue.jks. This value can be edited by the TENANT administrator. For more information, refer the authentication settings section in Configuring Administrative Preferences. SPKey Store Password The keystore password. In the prerequisite steps example, this is myPassword.SPKey Store Alias The keystore alias. In the prerequisite steps example, this is server. - Download the SP metadata file by clicking Download SP Metadata.
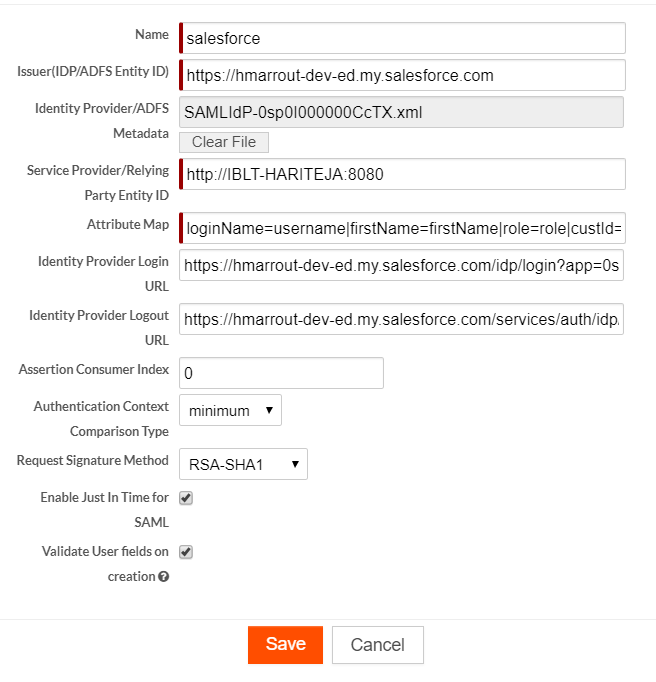
- Specify the following values to configure a Platform tenant to authenticate users using SAML or ADFS:
Default Setting: Selecting the Default UI field indicates the authentication profile that is currently set as a default UI authentication type. However, there is no compulsion that only one authentication profile should be the default for the UI authentications.
| Field | Description | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| Name | The name for the SAML configuration. | ||||||||
| Issuer (IDP/ADFS Entity ID) | This is the value of the entityID attribute of the EntityDescriptor element in the
IdP metadata file. This is a mandatory field. |
||||||||
| Identity Provider/ADFS Metadata | The IdP Metadata file. | ||||||||
| Service Provider EntityID/Relying Party Entity ID | The entity ID of the service provider. This
is a mandatory field. This is the value of the entityID attribute of the EntityDescriptor element in the SP
metadata file. |
||||||||
| Attribute Map | A pipe-separated mapping of the attributes in
the form integration name in Platform=attribute name sent from IdP. A user
can choose to map more than one attribute. The attribute loginName is the only required and
compulsory field to be mapped. You can also choose to add more
Attribute Mappings. For example: firstName=givenName|lastName=sn|loginName=uid|city=city |
||||||||
| Identity Provider Login URL | The URL the users of the tenant should use
to initiate SAML login. This is the value of the Location attribute in the SingleSignOnService element for
the HTTP-POST binding in the
IdP metadata file. |
||||||||
| Identity Provider Logout URL | A custom URL can be configured by the SAML customer administrator to redirect the user after logout. | ||||||||
| Assertion Consumer Index | The index of the URLs to be used in the SP metadata. In general, multiple URLs are not supported by most of the IdPs, so you can set this to the default of 0. | ||||||||
| Authentication Context Comparison Type | A comparison attribute on the AuthnContext
request parameter to indicate how an authentication context
should be evaluated. The authentication context will be
evaluated based on the relative strengths of the authentication
context classes specified in the AuthnContext request and the
authentication methods offered by an IdP. The four available comparison values are - better, exact, maximum, and minimum. If no value is specified, it will default to minimum . See setAuthentication and getAuthentication for more information. |
||||||||
| Request Signature Method | A signature method alogorithm to be used to
sign the request being sent to the IDP. You can select RSA-SHA1 or RSA-SHA256. The default value is
RSA-SHA1. |
||||||||
| Enable Just-In-Time for SAML |
When enabled, new application accounts are created on the fly by utilizing SAML assertions, thus eliminating manual account creations for every new user. With Just-In-Time enabled, the new user accounts are created dynamically by the first time users themselves upon the SAML based Platform SSO portal. See Just-in-Time Provisioning, for more information. |
||||||||
| Validate User Fields on creation |
If enabled, field format, mandatory fields and unique fields are validated on record creation for all the user fields including the below mentioned mandatory fields. If disabled (not recommended) and if any of the below mentioned mandatory fields are missing, an error is prompted without any field validations taking place. However, editing the record in the UI validates the data in any subsequent edit. The below listed mandatory fields are required by a user object while creating a record:
|
samlAuthnContextComparison will return the set comparison value
for getAuthentication REST API.
The following screen shows the properties for a sample configuration using Salesforce: