PGP Encryption
The platform enables PGP encryption by generating a public-private key pair at the instance level. The public key is made available for tenant admins to download and share with end users. Users must encrypt files with this public key before uploading them to the SFTP server.
During import, the platform identifies encrypted files, locates the private key, and decrypts the contents before processing. This ensures secure file transfer and data confidentiality.
Batch Jobs
The SFTP Batch Job is currently enhanced to support optional PGP encryption.
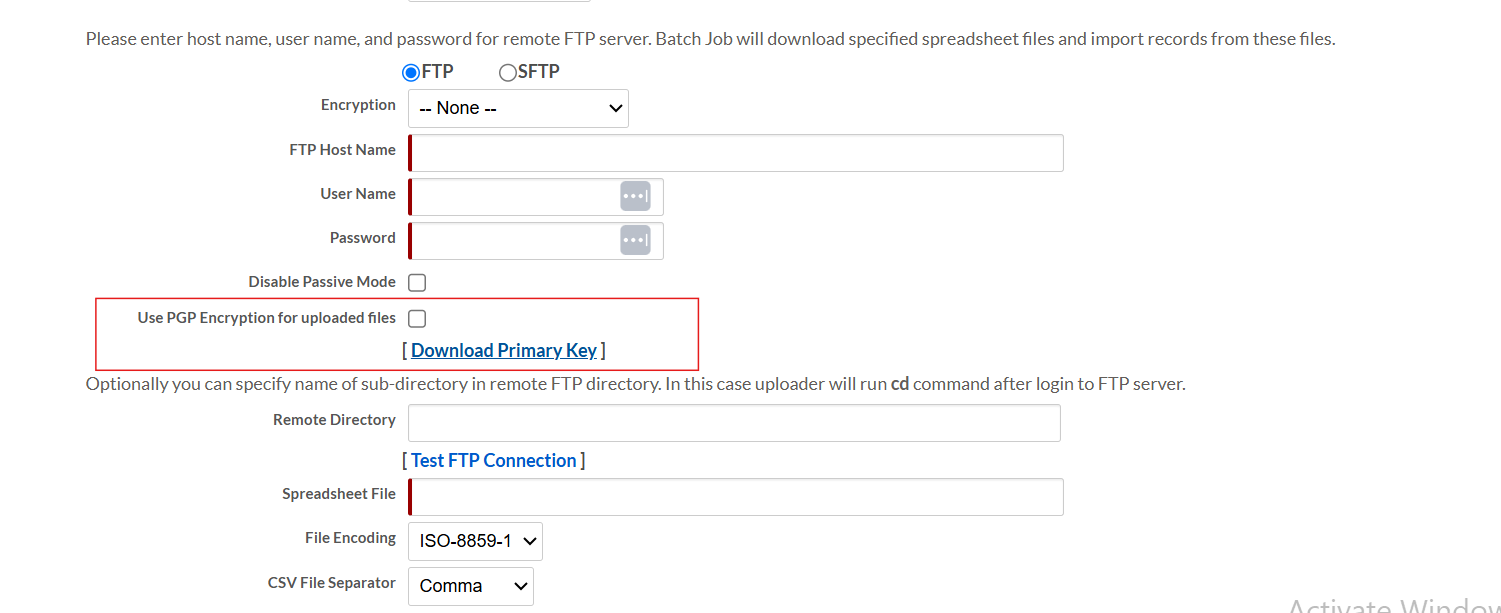
-
The Use PGP Encryption for uploaded files checkbox allows users to enable PGP for individual SFTP import jobs. Once enabled, the platform mandates that the files uploaded for a specific task must be encrypted using the specified public key.
-
The Download Primary Key option enables users to download the public key, ensuring they can encrypt their files accurately. This update is backward-compatible and continues to support non-encrypted jobs when the PGP option is not selected.
Generating PGP Encryption Public Key
To generate and place PGP keys for privately owned instances, do the following:
-
From the platform’s tomcat folder, navigate to the
libfolder, where therb_util.jaris present. -
Open the Command Prompt from this directory and enter the following command to generate the key.
-
Command for Windows Machine:
java -cp bcpg-jdk15on-1.70. jar; bcprov-jdk15on-1.70. jar; rb_util. jar com. rb. util. system. SystemKeyGenerator <<PATH_TO_SAVE_THE_GENERATED_KEY> 2 <USER_EMAIL_ID>
-
Command for Linux Machine:
java -cp bcpg-jdk15on-1.70.jar:bcprov-jdk15on-1.70.jar:rb_util.jar com.rb.util.system.SystemKeyGenerator .\ 2 dummy@organization.com
-
-
The CMD prompts the following message:
PGP Key file has been generated at location: <<GIVEN_LOCATION>>pgp_secret.asc
-
Place
pgp_secret.ascon any master node. After placing the key file, restart only that node. For example:tomcat/rollbase/config/security
Note: A full instance restart is not required.
Encrypting a File Using the Public Key
Before proceeding with encryption, it is essential to import the key file into the GnuPG keyring by utilizing the following command:
gpg --import <Path to the key>pgp_secret.asc
To ensure secure transmission of sensitive data, files must be encrypted using a PGP public key. The encrypted file should have the .gpg.csv extension.
To encrypt a file using the public key, do the following:
-
Use the gpg command-line tool to encrypt the file with the intended recipient’s public key.
gpg --output <output_file>.gpg.csv --encrypt --recipient "<Key ID or Email>" <path_to_input_file>
For Example:
gpg --output encrypted_file.gpg.csv --encrypt --recipient "youremailaddress@domain.com" C:\Users\YourUserName\Path\FileName.csv

